As cryptocurrency adoption grows, so does the variety of scams concentrating on unsuspecting customers. In 2025, one of the crucial regarding developments has been the rise of Crypto Drainers-as-a-Service (DaaS), a brand new breed of cybercrime that makes it simpler than ever for scammers to steal digital belongings.
Drainers are malicious instruments designed to empty crypto wallets by tricking customers into approving transactions that give scammers entry to their funds. What makes Crypto Drainers-as-a-Service particularly harmful is that it permits anybody, even these with little technical ability, to launch these assaults. For a charge, you should buy or hire drainers on the darkish internet or Telegram teams, full with easy-to-use dashboards, phishing templates, and even buyer assist.
On this article, we’ll break down how Crypto Drainers-as-a-Service works, who’s utilizing them, and most significantly, how one can defend your self from turning into a sufferer.
How does DaaS work as a plug-and-play rip-off toolkit?
Crypto Drainers-as-a-Service (DaaS) function like pre-packaged rip-off toolkits, providing cybercriminals a fast and simple technique to steal digital belongings. These kits include ready-to-use phishing web sites, faux pockets interfaces, and scripts that exploit pockets permissions, notably on Ethereum and different EVM-compatible blockchains.
Right here’s the way it sometimes works:
The scammer pays to entry a drainer service or subscribes to a revenue-sharing mannequin.
They’re given a phishing template mimicking fashionable dApps, NFT mints, or crypto companies.
Victims are lured to the phishing web site through faux advertisements, social media posts, Discord messages, or compromised verified accounts.
As soon as a consumer connects their pockets and unknowingly indicators a malicious transaction, the drainer script is triggered, instantly transferring the contents of the pockets to the scammer’s handle.
DaaS vs. Conventional Crypto Scams
Crypto Drainers-as-a-Service (DaaS) differ from conventional crypto scams in supply technique, execution pace, and plenty extra:
[Insert Image 1]
Whereas conventional phishing depends on tricking victims into giving up login credentials, DaaS kits exploit the way in which wallets deal with good contract permissions. This makes them quicker and, in lots of circumstances, more durable for common customers to detect earlier than it’s too late.
How These Scams Function
DaaS typically mimic authentic Web3 tasks, NFT mints, or fashionable DeFi platforms. Right here’s how they sometimes unfold:
Step-by-Step of a DaaS Rip-off
Phishing Hyperlink or Faux Web site
The crypto rip-off begins when the attacker distributes a phishing hyperlink through compromised social media accounts, Discord channels, faux advertisements, or direct messages. These hyperlinks result in web sites that completely mimic authentic platforms (like NFT mint pages or DeFi dashboards).
Sufferer Connects Their Pockets
As soon as on the location, the unsuspecting consumer is prompted to attach their crypto pockets. The whole lot seems regular. The location might even have countdown timers or buzzwords like “unique drop” to create urgency.
Malicious Sensible Contract Execution
After the pockets is linked, the location methods the consumer into signing a transaction. However as a substitute of minting an NFT or claiming a token, the consumer is unknowingly giving the attacker permission to entry or switch funds from their pockets.
Draining the Pockets
The drainer script robotically executes the malicious contract, immediately draining tokens, NFTs, or stablecoins to an handle managed by the scammer. Generally, there’s no technique to reverse the transaction as soon as it’s confirmed on-chain.
In January 2025, an lively phishing marketing campaign focused high-profile X accounts, together with these of U.S. political figures, journalists, and cryptocurrency organizations. Compromised accounts have been used to advertise fraudulent actions, exploiting the belief of their followers.
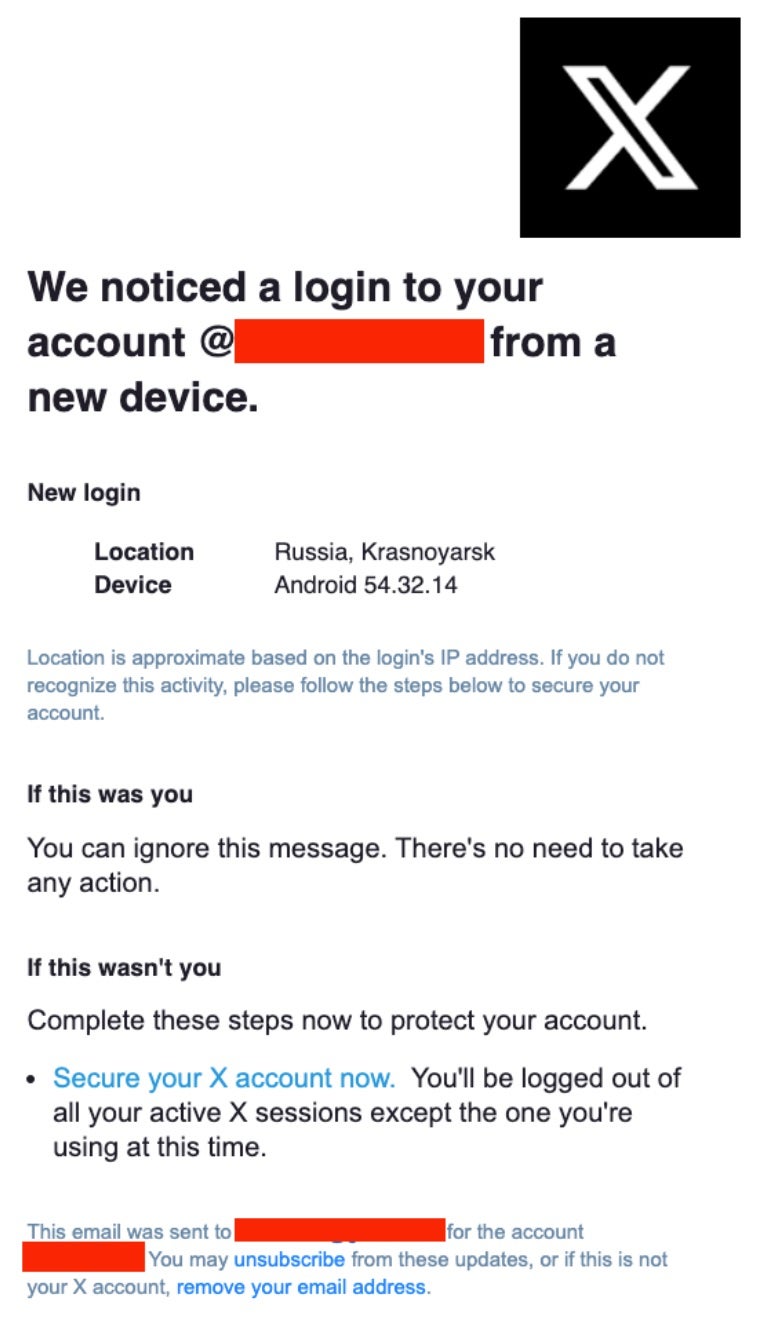
Who’s Behind Crypto Drainers-as-a-Service?
This ecosystem contains two essential gamers: expert builders who create and promote drainer kits, and associates or novice scammers who deploy these instruments to steal digital belongings.
Builders: The Architects of DaaS
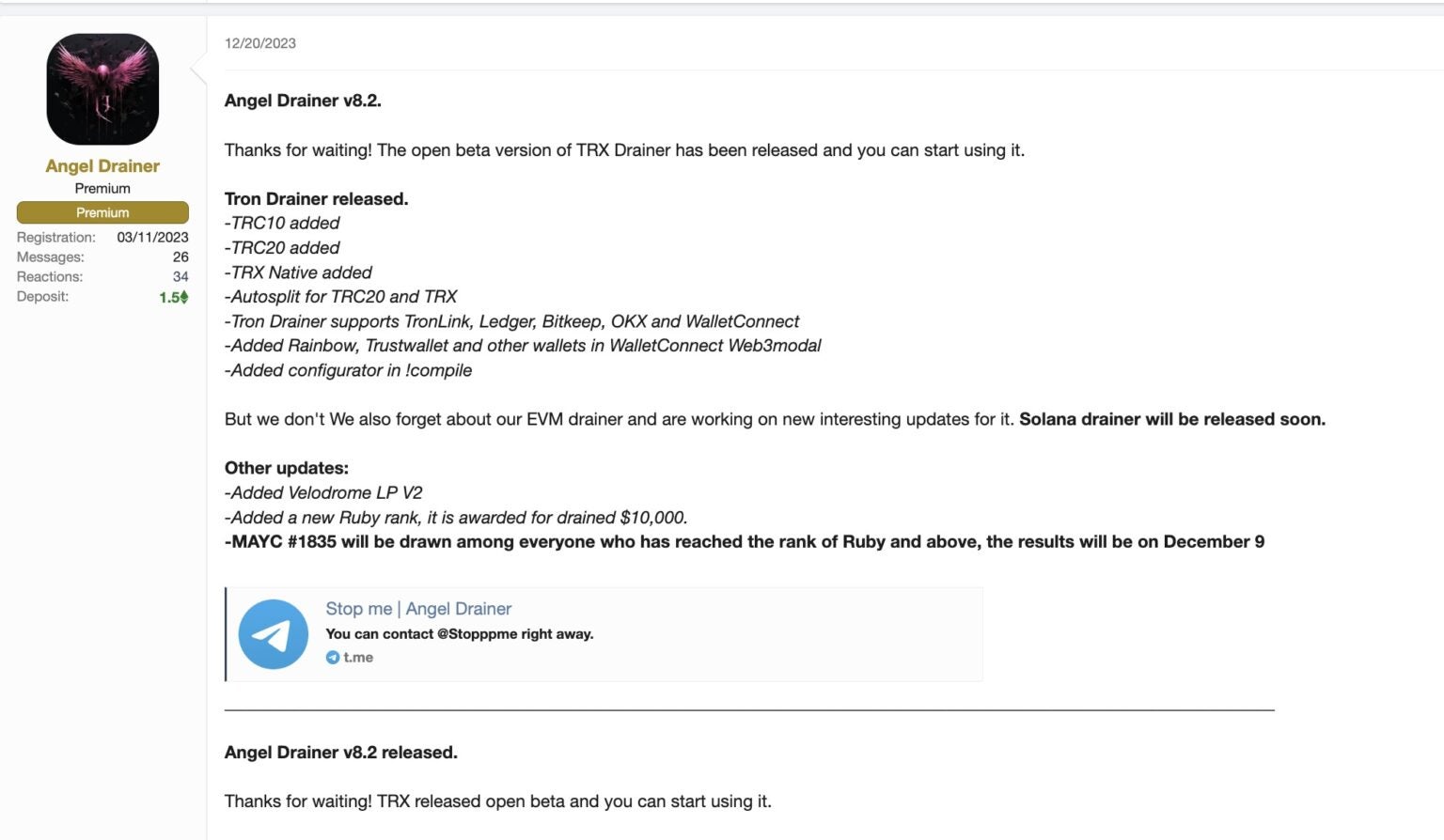
Skilled cybercriminals develop subtle drainer kits, packaging them with user-friendly interfaces, customizable phishing templates, and automatic scripts. These kits are offered or rented on darkish internet boards and Telegram channels. Notable examples embrace:
Angel Drainer: Rising round August 2023, it affords instruments and companies marketed throughout Telegram by identified risk actors. Associates are required to make an preliminary deposit of between $5,000 and $10,000, with operators taking a 20% minimize of the stolen funds.
Rugging’s Multi-chain Drainer: Helps 20 totally different crypto platforms and entices associates by providing low charges, round 5-10% of the associates’ features.
These builders typically present common updates to evade detection and will supply buyer assist by means of encrypted channels.
Associates: The Executors of Scams
Associates, starting from low-skilled scammers to organized cybercriminal teams, buy or hire these drainer kits to conduct phishing campaigns. They distribute malicious hyperlinks through compromised social media accounts, faux advertisements, or direct messages, luring victims to attach their wallets to fraudulent web sites. As soon as a sufferer authorizes a transaction, the drainer script transfers belongings to the scammer’s pockets.
Monetization Fashions
Crypto Drainers-as-a-Service operators make use of varied monetization methods:
Subscription Charges: Associates pay a recurring charge for entry to the drainer package and related companies.
Income Sharing: Operators take a share (sometimes 5-25%) of the stolen belongings. As an example, in campaigns utilizing the CLINKSINK drainer, operators took round 20% of the associates’ features.
One-Time Funds: A flat charge grants associates lifetime entry to the drainer package.
This commercialized mannequin lowers the barrier to entry for cybercriminals, enabling widespread, coordinated assaults throughout the crypto ecosystem.
Why These Assaults Are Rising
Right here’s a breakdown of why these scams are rising:
Low Barrier to Entry
Crypto Drainers-as-a-Service kits are designed to be user-friendly and require no coding or technical abilities. Even inexperienced scammers can:
Purchase or hire a ready-to-use drainer toolkit.
Customise phishing templates with drag-and-drop interfaces.
Use step-by-step guides offered by builders through Telegram or darkish internet boards.
This ease of entry turns anybody into a possible risk actor, fueling the expansion of amateur-driven assaults.
Anonymity and Decentralization
The decentralized nature of crypto permits attackers to maneuver stolen funds with out conventional oversight:
Nameless Wallets: No want for KYC/id verification means stolen funds are more durable to hint.
Mixers and Cross-Chain Bridges: Instruments like Twister Money or cross-chain bridges are used to launder and obscure stolen crypto.
Lack of Regulation: Various world legal guidelines create loopholes scammers can exploit.
This anonymity incentivizes malicious actors to maintain launching assaults with minimal concern of authorized penalties.
Excessive-Worth, Excessive-Exercise Targets
Because the crypto ecosystem grows, so does the quantity and worth of potential victims:
NFT Drops: Widespread collections entice 1000’s of keen patrons, typically tricked into signing malicious contracts on faux mint websites.
DeFi Protocols: Customers typically have massive sums locked in good contracts, making them profitable targets.
Meme Cash and Hype Tokens: These entice retail buyers who might lack technical know-how and fall for FOMO-driven scams.
Excessive-traffic moments, like trending NFT mints or new token launches, create excellent situations for DaaS scams to succeed.
Easy methods to Shield Your Pockets
DaaS scams have gotten extra subtle, making it extra vital than ever to guard your pockets. Right here’s tips on how to safeguard your belongings:
Keep away from Connecting to Suspicious dApps
Many scams begin with a phishing hyperlink to a faux dApp. To remain protected:
Double-check URLs earlier than connecting your pockets, particularly throughout NFT drops or token launches.
By no means join your pockets to a dApp shared by means of DMs, sketchy emails, or unknown Discord/Twitter accounts.
Utilizing platforms like Chainabuse or Web3 is Going Simply Nice to test for crypto rip-off studies.
Use {Hardware} Wallets and Transaction Previews
{Hardware} wallets like Ledger or Trezor hold your personal keys offline, including an additional layer of safety.
Mix with trusted browser extensions (Rabby or MetaMask) that present transaction previews earlier than you signal.
All the time learn transaction particulars. Crypto Drainers-as-a-Service kits typically disguise malicious approvals in deceptive prompts.
Monitor and Revoke Token Permissions
Sensible contracts typically request approval to entry your belongings indefinitely. Use token approval monitoring instruments to remain in management:
[Insert Image 2]
Evaluation your pockets commonly and revoke entry to dApps you now not use.
Keep Knowledgeable
Scammers evolve quick, so ought to your consciousness. To remain forward:
Observe trusted safety accounts like @SlowMist_Team or @CertiK on Twitter/X.
Monitor official channels for dApps and NFT tasks.
Be part of communities like r/ethereum, r/CryptoCurrency, or Discord safety channels for real-time crypto rip-off alerts.
By combining these proactive steps, you’ll be able to dramatically cut back your publicity to Crypto Drainers-as-a-Service scams and different crypto threats. All the time belief your instincts. If one thing feels off, don’t join or signal.
Closing Ideas
Within the crypto world, staying cautious and practising good pockets hygiene is crucial to defending your belongings. These scams thrive as a result of they exploit rushed choices and a lack of know-how. So at all times double-check the websites you go to, scrutinize each pockets permission request, and keep away from connecting your pockets to unknown or suspicious platforms.
Past private vigilance, leveraging out there safety instruments can drastically improve your safety. Use {hardware} wallets to maintain your personal keys offline, commonly assessment and revoke pointless permissions with companies like revoke.money, and keep knowledgeable by means of trusted crypto safety communities.
Keep in mind, in crypto, safety means self-sovereignty; you management your funds, but in addition your dangers. Combining cautious habits with the fitting instruments will enable you navigate the crypto area extra safely and confidently. Staying alert, knowledgeable, and vigilant is your greatest defence towards scammers. Shield your pockets like your most dear asset, as a result of it actually is.
Disclaimer: This text is meant solely for informational functions and shouldn’t be thought-about buying and selling or funding recommendation. Nothing herein needs to be construed as monetary, authorized, or tax recommendation. Buying and selling or investing in cryptocurrencies carries a substantial threat of economic loss. All the time conduct due diligence.
If you want to learn extra articles like this, go to DeFi Planet and comply with us on Twitter, LinkedIn, Fb, Instagram, and CoinMarketCap Group.
Take management of your crypto portfolio with MARKETS PRO, DeFi Planet’s suite of analytics instruments.”
The publish Crypto Drainers-as-a-Service: How These New-Age Scams Are Concentrating on Your Pockets appeared first on DeFi Planet.








